Crypt Cloud+: Secure and Expressive Data Access Control for Cloud Storage
- Blog
- Discount New Year
- Final Year Matlab Proj
- final year proj
- Final Year Proj for Computer Science
- Final Year Proj for Electronics
- Final Year Proj for Information Technology
- Mini Projects
- Order cancellation
- Privacy policy
- Project Categories
- Return Policy
- Terms and Conditions
- Terms of use
- Tutorials
- Discount
-
Projects
- Embedded
- Java
-
Matlab
- 5G Communication/Signal Processing
- ANTENNA Design
- Artificial intelligence
- Automation & Fault Detection
- Cryptography- Authentication
- Cyber Security
- Data Analytics
- Deep Learning
- Digital Image Processing
- GAN
- Machine Learning
- Matlab Hardware Interface
- Medical Imaging
- Natural Language Processing
- Robotic OS (ROS) - Hardware
- Robotic OS (ROS) - Simulation
- Web Application
- Mechanical
- Python
- VLSI
- Workshops
- Internship
Your shopping cart is empty!
Product Description
Aim:
The main aim of this
project is to provide integrity of an organization data which is in public
cloud.
Synopsis:
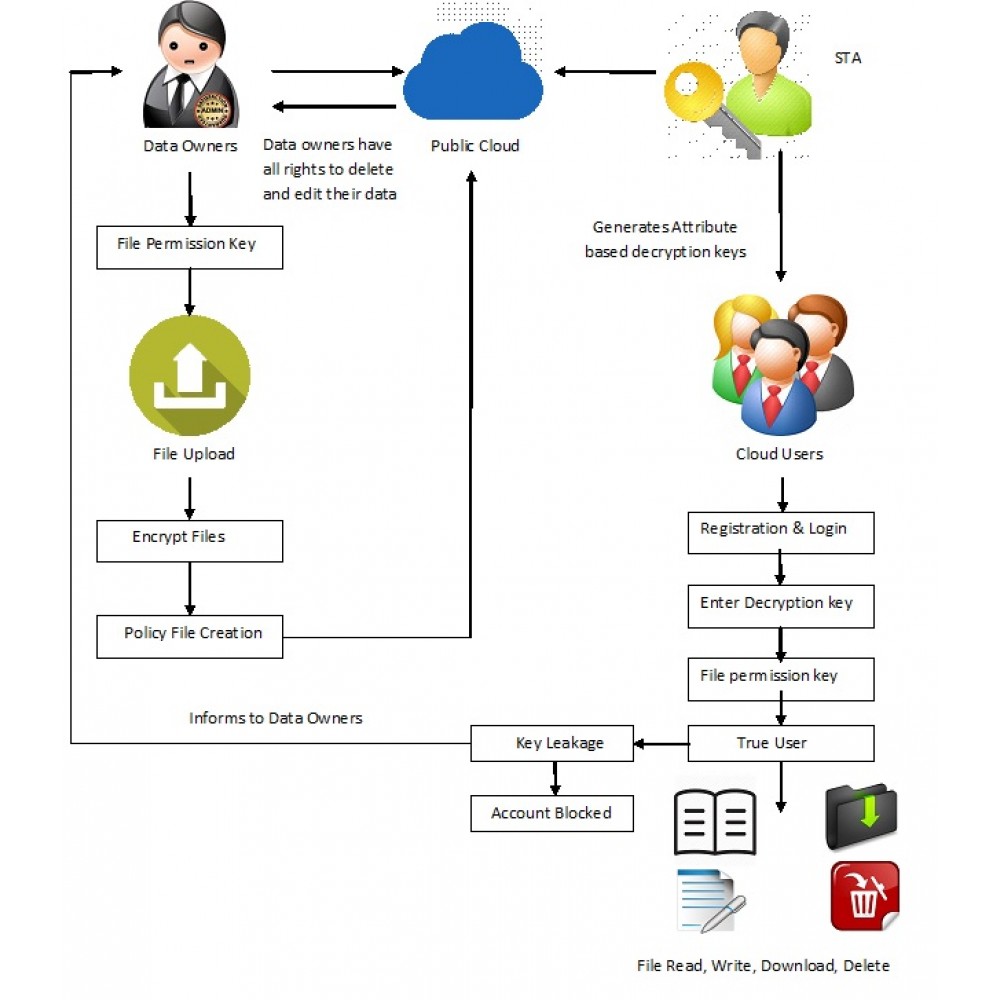
Data owners will
store their data in public cloud along with encryption and particular set of
attributes to access control on the cloud data. While uploading the data into
public cloud they will assign some attribute set to their data. If any
authorized cloud user wants to download their data they should enter that
particular attribute set to perform further actions on data owner’s data. A
cloud user wants to register their details under cloud organization to access
the data owner’s data. Users want to submit their details as attributes along
with their designation. Based on the user details Semi-Trusted Authority
generates decryption keys to get control on owner’s data. An user can perform a lot of operations over
the cloud data. If the user wants to read the cloud data he needs to be
entering some read related attributes, and if he wants to write the data he
needs to be entering write related attributes. Foe each and every action user
in an organization would be verified with their unique attribute set. These
attributes would be shared by the admins to the authorized users in cloud
organization. These attributes will be stored in the policy files in a cloud.
If any user leaks their unique decryption key to the any malicious user data
owners wants to trace by sending audit request to auditor and auditor will
process the data owners request and concludes that who is the guilty.
Proposed System:
In this work, we have addressed the challenge of
credential leakage in CP-ABE based cloud storage system by designing an
accountable authority and revocable Crypt Cloud which supports white-box
traceability and auditing (referred to as Crypt Cloud+). This is the first
CP-ABE based cloud storage system that simultaneously supports white-box
traceability, accountable authority, auditing and effective revocation.
Specifically, Crypt Cloud+ allows us to trace and revoke malicious cloud users
(leaking credentials). Our approach can be also used in the case where the
users’ credentials are redistributed by the semi-trusted authority.
When you order from finalyearprojects.in, you will receive a confirmation email. Once your order is shipped, you will be emailed the tracking information for your order's shipment. You can choose your preferred shipping method on the Order Information page during the checkout process.
The total time it takes to receive your order is shown below:

The total delivery time is calculated from the time your order is placed until the time it is delivered to you. Total delivery time is broken down into processing time and shipping time.
Processing time: The time it takes to prepare your item(s) to ship from our warehouse. This includes preparing your items, performing quality checks, and packing for shipment.
Shipping time: The time for your item(s) to tarvel from our warehouse to your destination.
Shipping from your local warehouse is significantly faster. Some charges may apply.
In addition, the transit time depends on where you're located and where your package comes from. If you want to know more information, please contact the customer service. We will settle your problem as soon as possible. Enjoy shopping!
Download Abstract
Click the below button to download the abstract.
Package Includes
Software Projects Includes
- Demo Video
- Abstract
- Base paper
- Full Project PPT
- UML Diagrams
- SRS
- Source Code
- Screen Shots
- Software Links
- Reference Papers
- Full Project Documentation
- Online support
The Delivery time for software projects is 2 -3 working days. Some of the software projects will require Hardware interface. Please go through the hardware Requirements in the abstract carefully. The Hardware will take 7-8 Working Days
Hardware Projects Includes
- Demo Video
- Abstract
- Base paper
- Full Project PPT
- Datasheets
- Circuit Diagrams
- Source Code
- Screen Shots & Photos
- Software Links
- Reference Papers
- Lit survey
- Full Project Documentation
- Online support
The Delivery time for Hardware
projects is 7-8 working days.
Mini Projects: Software Includes
- Demo Video
- Abstract
- Base paper
- Full Project PPT
- UML Diagrams
- SRS
- Source Code
- Screen Shots
- Software Links
- Reference Papers
- Full Project Documentation
- Online support
The
Delivery time for software Miniprojects is 2 -3 working days.
Mini Projects - Hardware includes
- Demo Video
- Abstract
- PPT
- Datasheets
- Circuit Diagrams
- Source Code
- Screen Shots & Photos
- Software Links
- Reference Papers
- Full Project Documentation
- Online
support
The Delivery time for Hardware Mini projects is 7-8 working days.