Aim:
Our study aims to develop a Blockchain-Enabled Secret Image Sharing (BC-SESIS) system that ensures secure, transparent, and tamper-proof storage and retrieval of sensitive image data, enhancing trust, privacy, and data integrity in wireless communication networks.
Abstract:
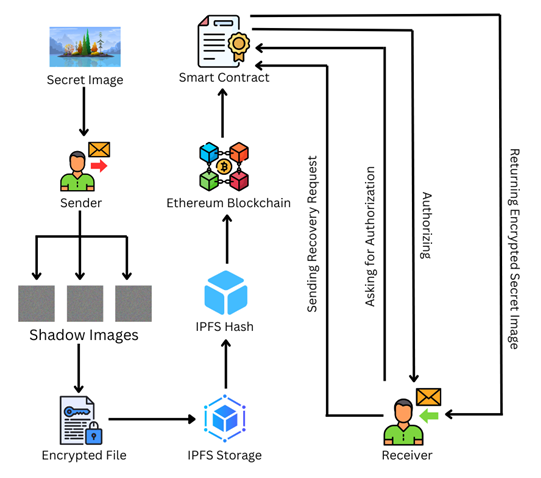
This project aims to develop a Secret Image Sharing (SIS) method, which is used to divide a secret image into multiple shadow images, where any subset of at least k shadow images can reconstruct the original image. Existing SIS techniques face challenges as shadow images can be tampered with or damaged during communication, leading to security risks. Blockchain technology offers a reliable solution for secure data communication and information protection. This paper introduces a Blockchain-based Secure and Efficient Secret Image Sharing (BC-SESIS) scheme for wireless networks. In this approach, shadow images are encrypted and stored on the blockchain, ensuring they cannot be altered or corrupted. A smart contract with identity authentication enables the (k, n) threshold restoration of the secret image. To reduce the computational load on users and smart contracts, the scheme uses outsourcing computation, where trusted agents handle the restoration process securely. Analysis and experiments show that BC-SESIS improves security and computational efficiency in wireless networks, making it a robust solution for secret image sharing.
Proposing System:
The proposed system enhances security by using AES encryption to securely encrypt the shadow images, ensuring faster encryption and decryption with strong protection against unauthorized access. AES improves efficiency by reducing computational time and complexity compared to polynomial encryption. The use of ECDSA ensures data integrity by signing the encrypted data, providing strong authentication and preventing tampering. The system leverages blockchain to securely store encrypted shadow images, ensuring tamper-proof access and transparency. Outsourcing the computational load to trusted miners further reduces the burden on users while maintaining security. Identity authentication through smart contracts ensures that only authorized users can participate in the restoration process. The decentralized storage through IPFS ensures efficient and secure storage, eliminating the risks of centralized data corruption. Overall, the proposed system offers a more secure, efficient, and reliable solution for secret image sharing in wireless networks.
Advantages:
The proposed system enhances security by using AES encryption, which ensures fast and strong protection against unauthorized access. ECDSA provides robust authentication and prevents tampering, guaranteeing data integrity. Additionally, outsourcing computation reduces the computational burden on users, while blockchain and IPFS offer secure, tamper-proof storage and decentralized access.



















Reviews
There are no reviews yet.